imunify360: Adding a firewall port(s) allow/override using CLI commands and/or config files
Since I have put my Plesk host behind a Cloudflare tunnel, I wish no longer to allow direct IP address access to the host.
On this page
OVH firewall vs OS firewall
In my case, I can use OVH’s firewall to block all access to the IP, but I can also use the host’s firewall to block all ports, in my case I let Imunify360 handle the IPTables
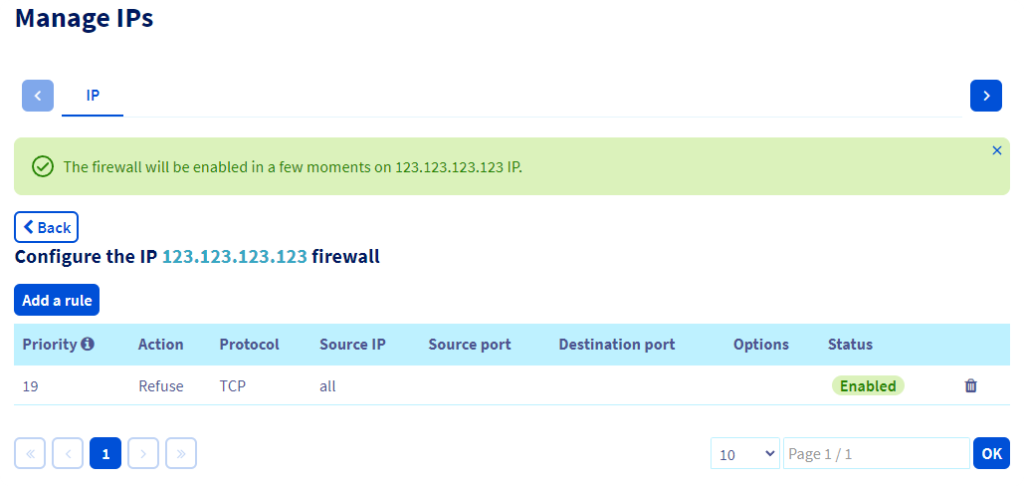
Imunify360 firewall
But before closing those ports with the firewall I needed a way to re-enable the ports if for whatever reason I needed direct access again (not using the Cloudflare tunnel or the tailscale tunnel) for me this would be the OVH KVM.
We have two options to achieve this
- Using the imunify360 CLI to add a port to the config
- Using the imunify360 config files to add a port (probably easier)
NOTE
I use the firewall in “all close, except specified” mode a.k.a port_blocking_mode: DENY
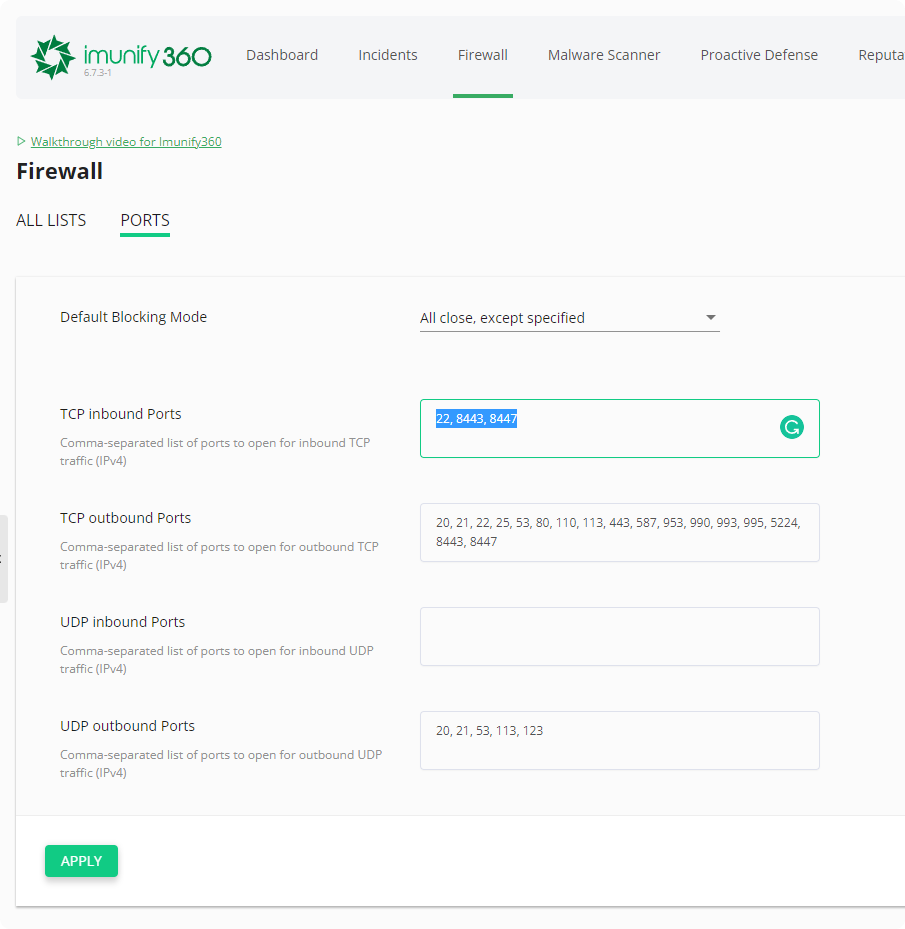
Using imunify360 CLI to add a port to the firewall config
at the moment of writing, there is no dedicated firewall command for the CLI.
So we require piping output and JQ magic to get the CLI to do what we want.
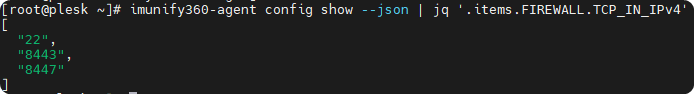
Get the current open ports with the imunify CLI:
imunify360-agent config show --json | jq '.items.FIREWALL.TCP_IN_IPv4'
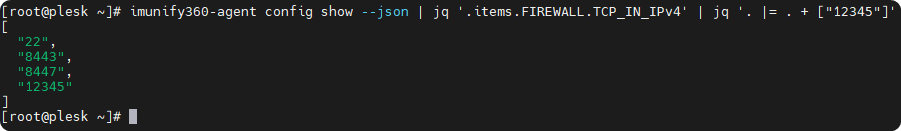
now we have to add our port to the list
jq '. |= . + ["12345"]' imunify360-agent config show --json | jq '.items.FIREWALL.TCP_IN_IPv4' | jq '. |= . + ["12345"]'
now we have to take that array of JSON and append it into TCP_IN_IPv4 object
imunify360-agent config show --json | jq '.items.FIREWALL.TCP_IN_IPv4' | jq '. |= . + ["12345"]' | jq -c '{FIREWALL: {TCP_IN_IPv4: .}}'
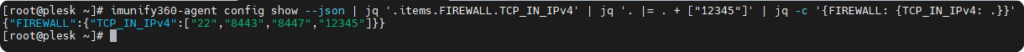
Now let’s get this into the config itself, which brings us to the final command
imunify360-agent config update $(imunify360-agent config show --json | jq '.items.FIREWALL.TCP_IN_IPv4' | jq '. |= . + ["8443"]' | jq -c '{FIREWALL: {TCP_IN_IPv4: .}}')
Testing the command
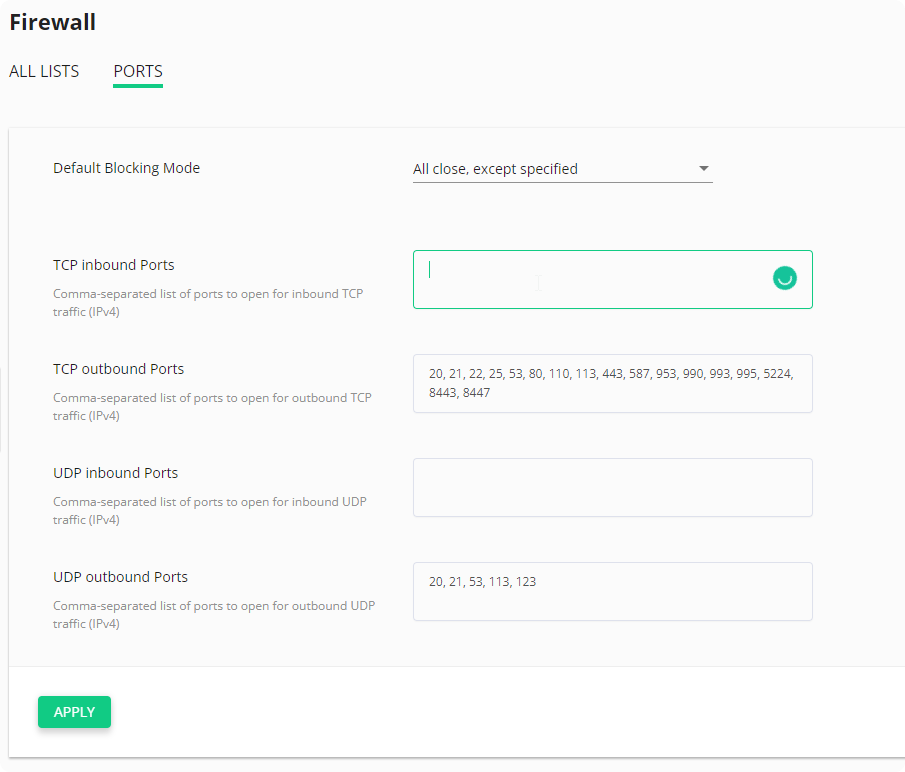
executing or CLI command and checking the interface
imunify360-agent config update $(imunify360-agent config show --json | jq '.items.FIREWALL.TCP_IN_IPv4' | jq '. |= . + ["8443"]' | jq -c '{FIREWALL: {TCP_IN_IPv4: .}}')
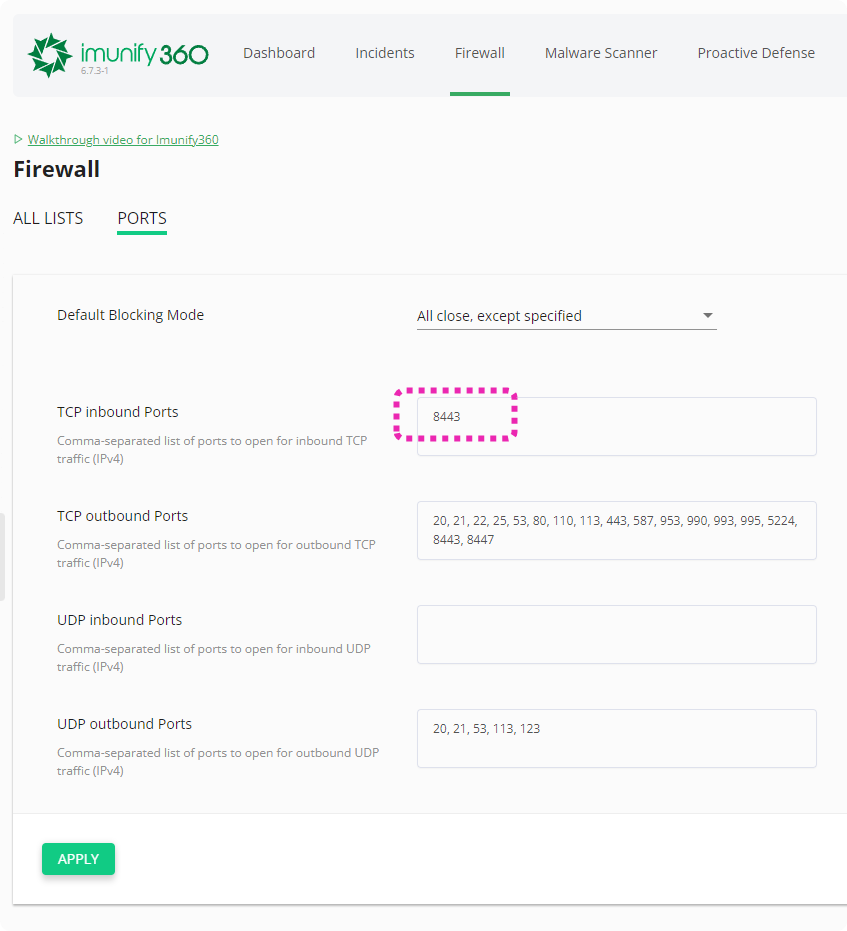
We can also request the current config and see if our port is there
imunify360-agent config show --json -v | grep -C 10 "FIREWALL"
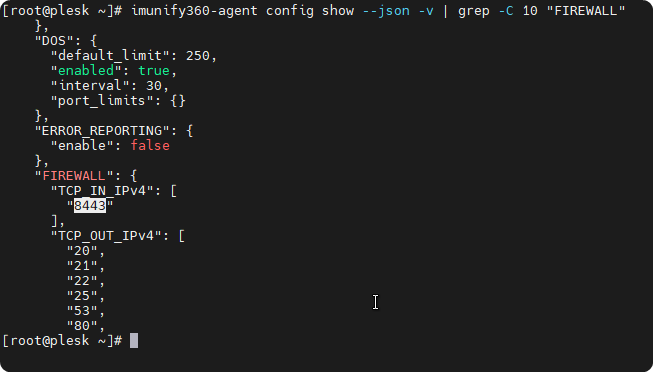
So that works! we can now use this command to enable our ports again in case we need direct IP access again and not over tunnels/vpn
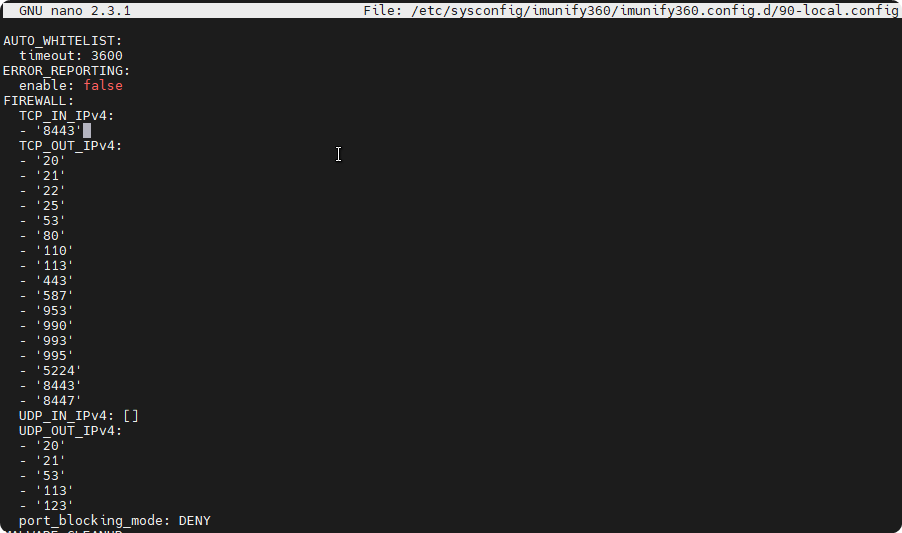
Using the imunify360 config files to add a port
I’m not too much of a fan of piping output to modifiers and back to inputs 🙃
Another way to open ports is by opening the ports in the config and restarting imunify.
there is an overridable config for imunify360
nano /etc/sysconfig/imunify360/imunify360.config.d/90-local.config
service imunify360 restart systemctl restart imunify360.service
both methods work!

