Setting up CloudFlare Zero Trust tunnels with Plesk
I was using firecove to reconfigure my OVH’s firewalls to only allow cloudflare connections, but there are better and newer ways! 🚀
Since I’m a CloudFlare customer already the entry bar for using CloudFlare’s new Zero Trust tunnels is low.
On this page
Steps to take
- Create unique local IP’s on our plesk server
- Assign the created IP to a website/domain
- Set up a tunnel in CloudFlare
- Set up cloudflared on our host
- Configure cloudflared with our API key from cloudflare
- Set up a public hostname in the tunnel
Updating Plesk to support CloudFlare zero trust tunnels
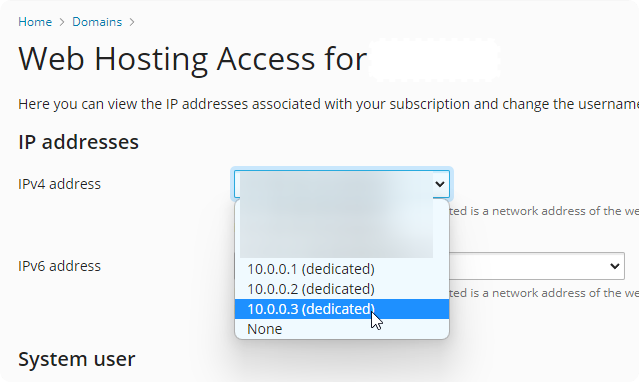
Maybe there is a better way of doing this, but to me it looked like adding local IP’s to my node (not routable) and marking them as dedicated was the way forward.
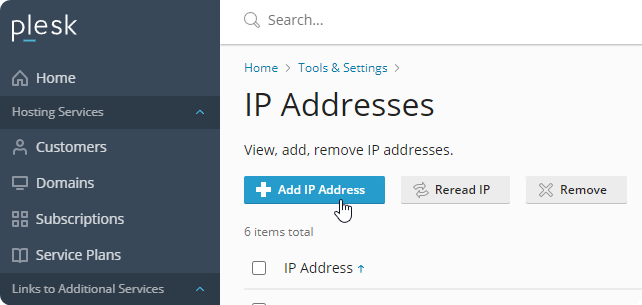
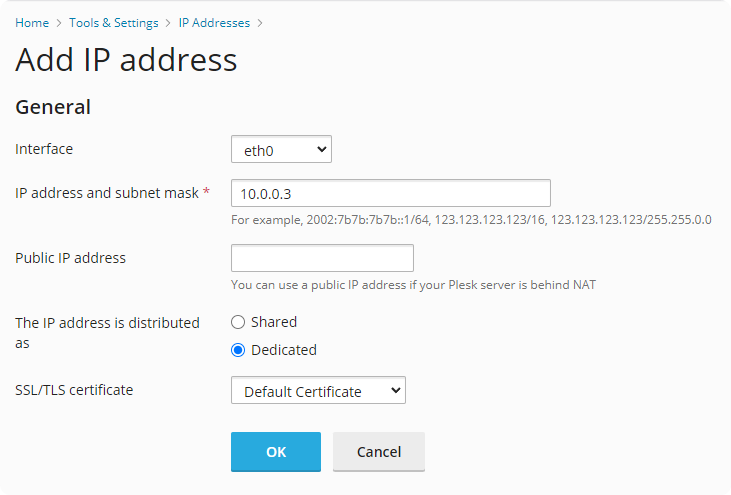
Pick whatever you want as an internal IP, I pick the 10 range, just have an unique IP per website, and make sure dedicated is selected
Now switch your domain/website “Home > Domains > [domain]” to the freshly made local IP
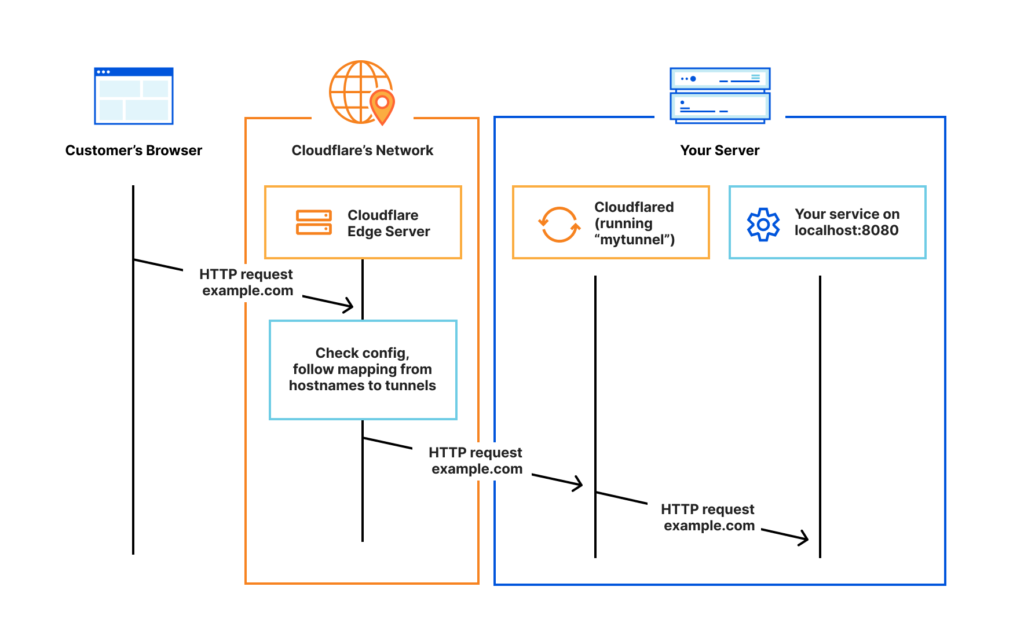
Setting up the CloudFlare zero trust tunnel
Head over to the CloudFlare zero trust panel
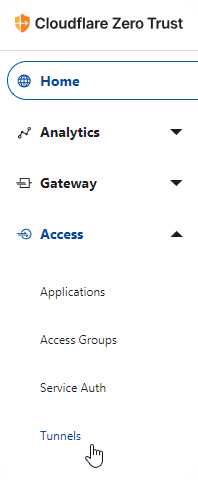
First, let’s set up a tunnel
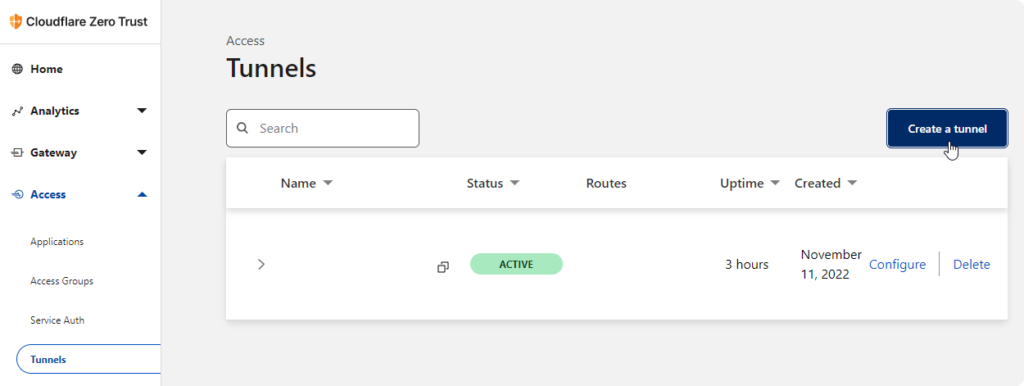
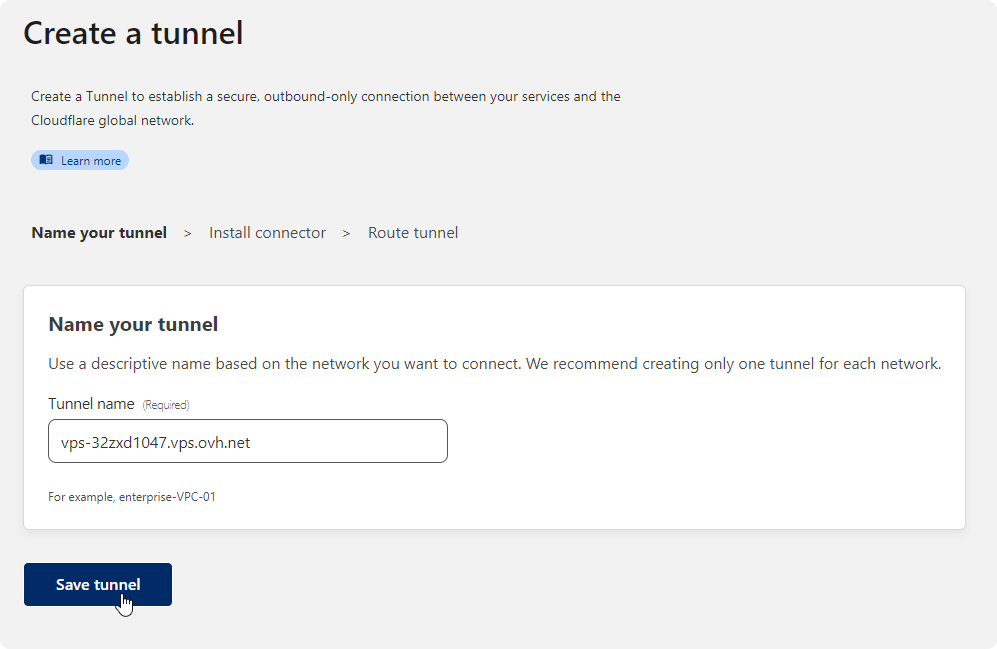
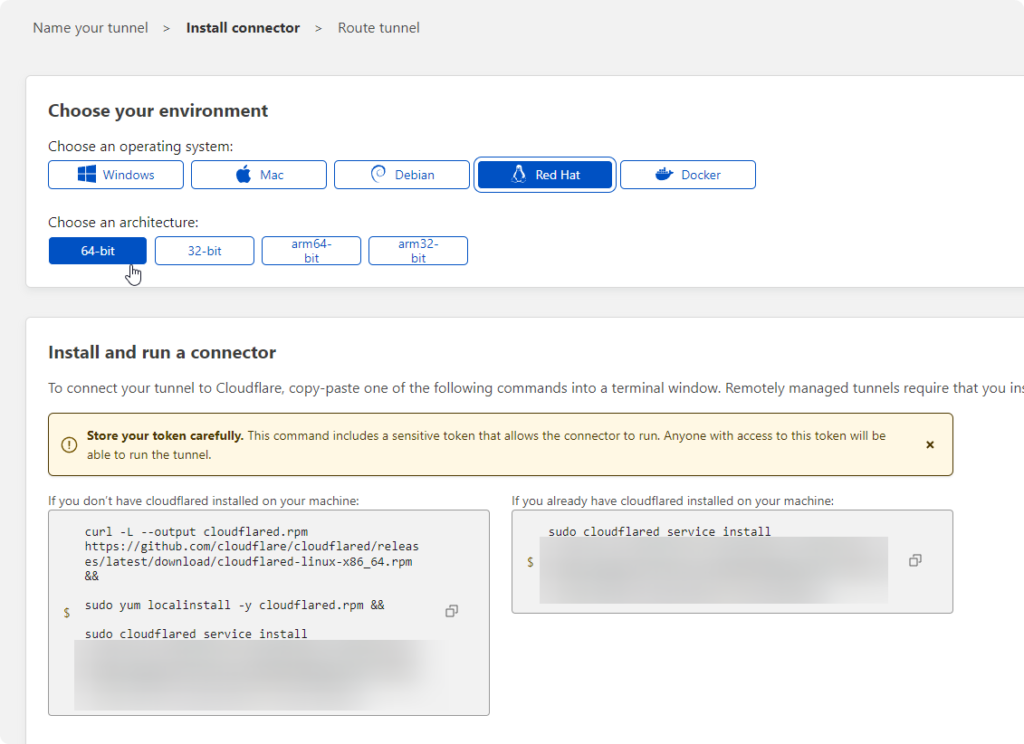
I do suggest NOT to run that curl command.
I suggest installing cloudflared with your hosts package manager (so it stays up to date if you have autoupdates enabled)
Installing cloudflared as a service with your package manager (for me AlmaLinux)
sudo dnf update sudo dnf config-manager --add-repo https://pkg.cloudflare.com/cloudflared-ascii.repo sudo dnf install cloudflared sudo cloudflared service install
Once you have your tunnel up and running, head over to the tunnel’s public hostnames
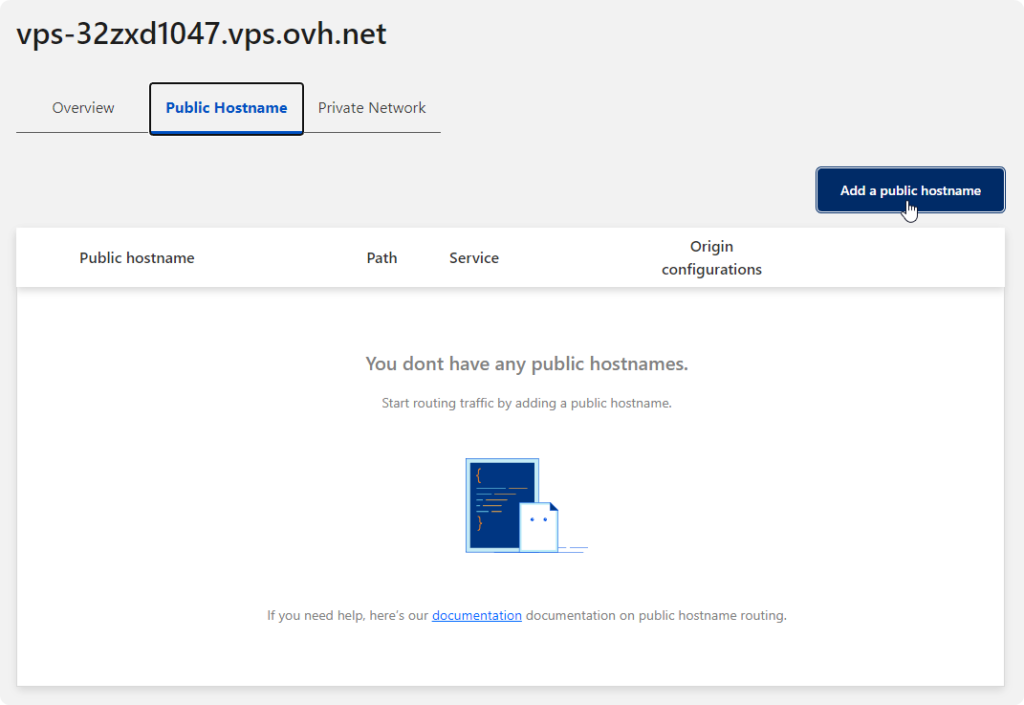
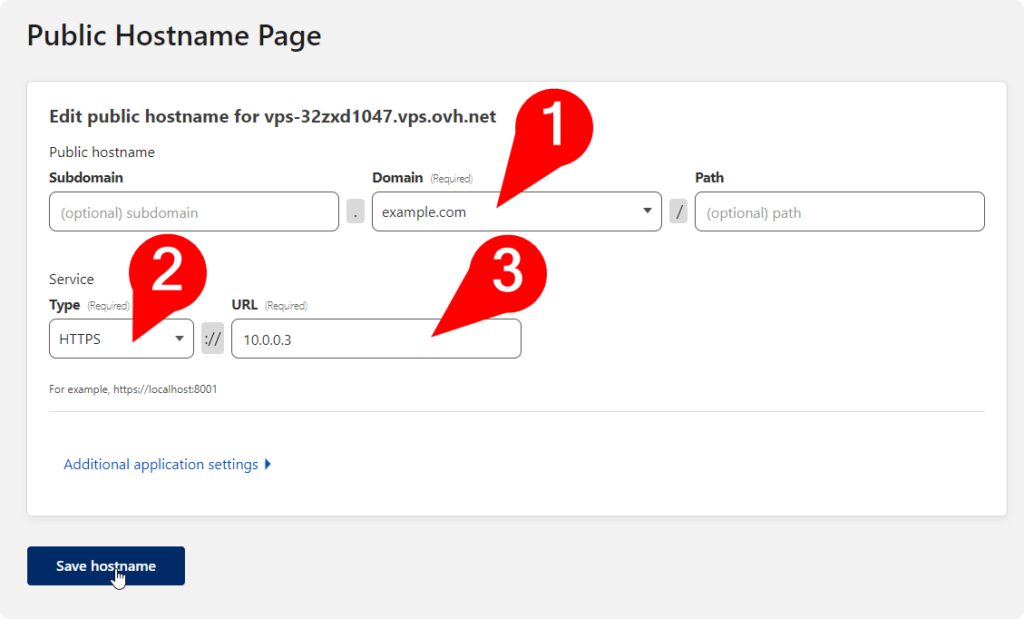
(2) pick the type, in my case I picked HTTPS.
(3) point to the local IP you assigned to the website earlier
It might error saying you already have an A record for whatever you are trying to set up, just delete that from your DNS settings and retry the save step.
give the DNS some time to propagate, and 🎉 you now no longer expose your web server to the public internet
Some more notes / things that you might have to do too!
railgun & cloudflared
If you have a railgun on your domain, disable that first 🤔 my cloudflare tunnel and my railgun were fighting 🥊 and I had to disable railgun
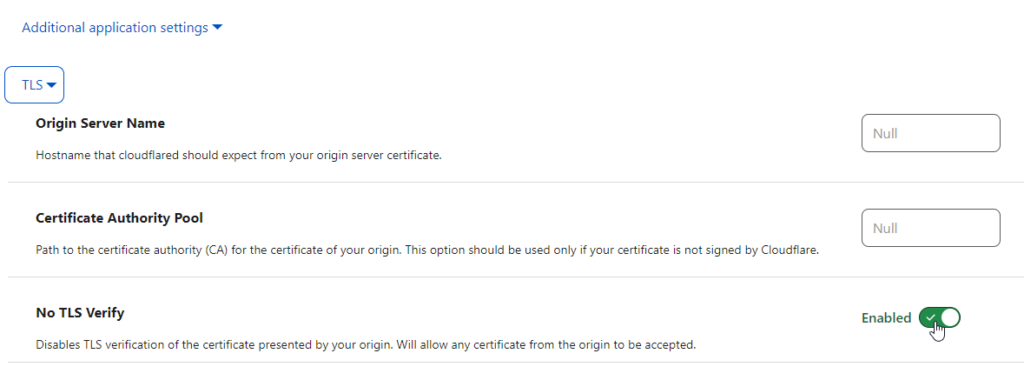
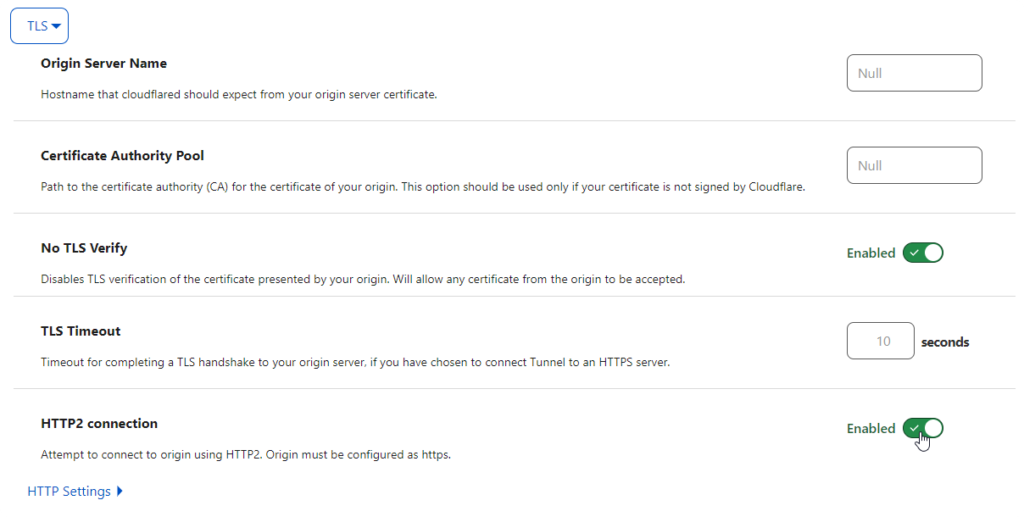
TLS verify / SSL errors
I was having some connectivity issues after adding a public hostname. Checking the logs of the cloudflared service showed there were certificate issues between the tunnel and the locally hosted website, so turn on No TLS Verify
journalctl -u cloudflared.service -f
under the problematic public hostname, enable No TLS verify
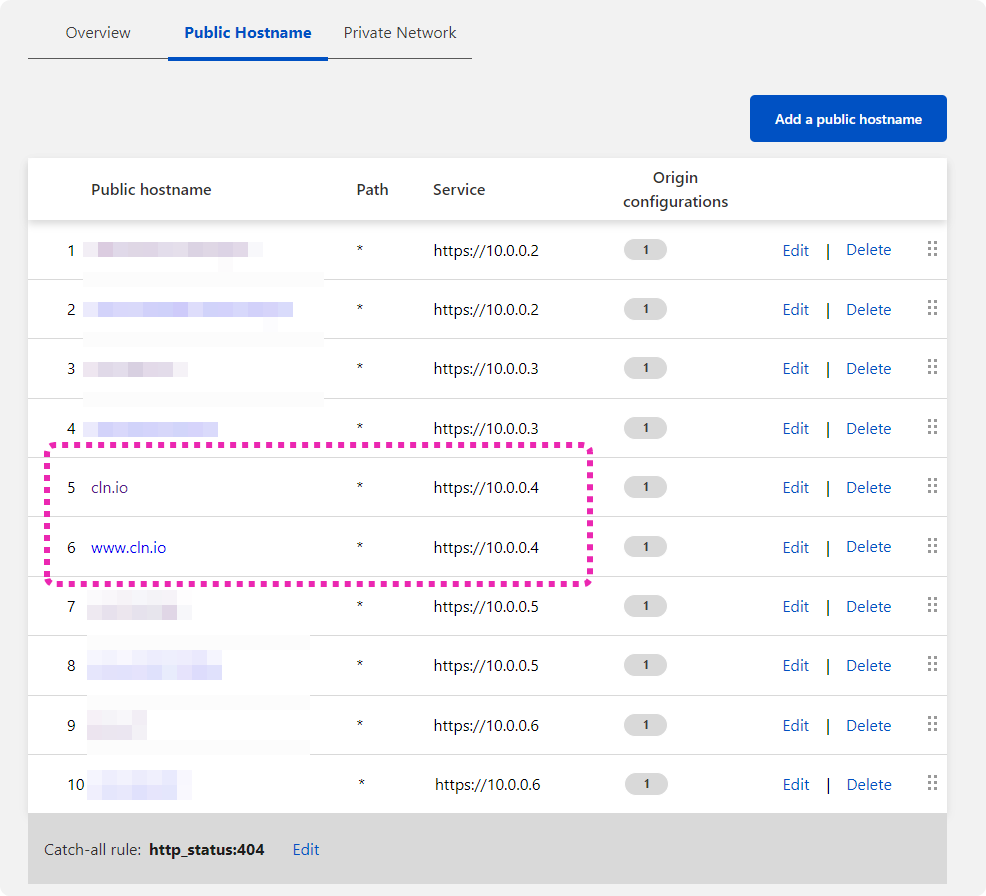
WWW / CNAME
a CNAME www -> @ did not seem to work for me, I had to add www. to my tunnel too
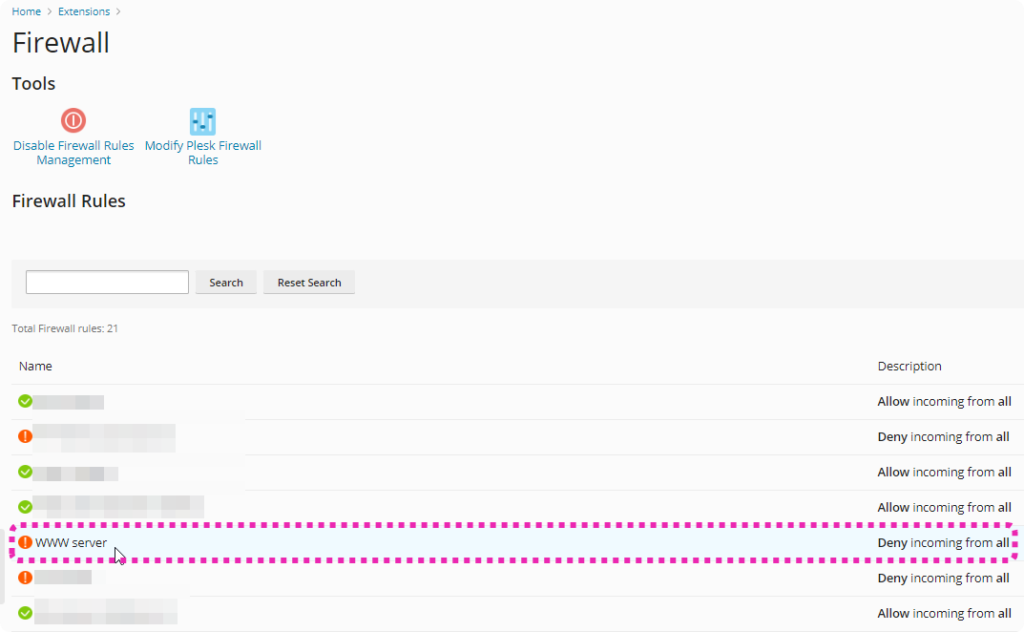
Disable your firewall rule for WWW
Once you have your tunnel up and running, I suggest to disable any incoming WWW traffic (80/443) in the firewall settings
Enable HTTP2 for the tunnel
Depending on your firewall, allow tunnel ports out
Since I work with outbound ports closed too, I had to allow some outbound ports for the Cloudflare tunnel to work ( their documentation )
| Destination | Port | Protocols |
|---|---|---|
region1.v2.argotunnel.com | 7844 | TCP/UDP (h2mux, http2, and quic) |
region2.v2.argotunnel.com | 7844 | TCP/UDP (h2mux, http2, and quic) |
api.cloudflare.com | 443 | TCP (HTTPS) |
update.argotunnel.com | 443 | TCP (HTTPS) |