Forcing DNS requests over AdGuard / Pi-hole with an Ubiquiti EdgeRouter firewall
With NAT Masquerades and DNAT rules.
On this page
My setup
- I have an EdgeRouter 4 sitting on 192.168.1.1
- I have an adguard instance on 192.168.1.4
- DHCP is done by the EdgeRouter
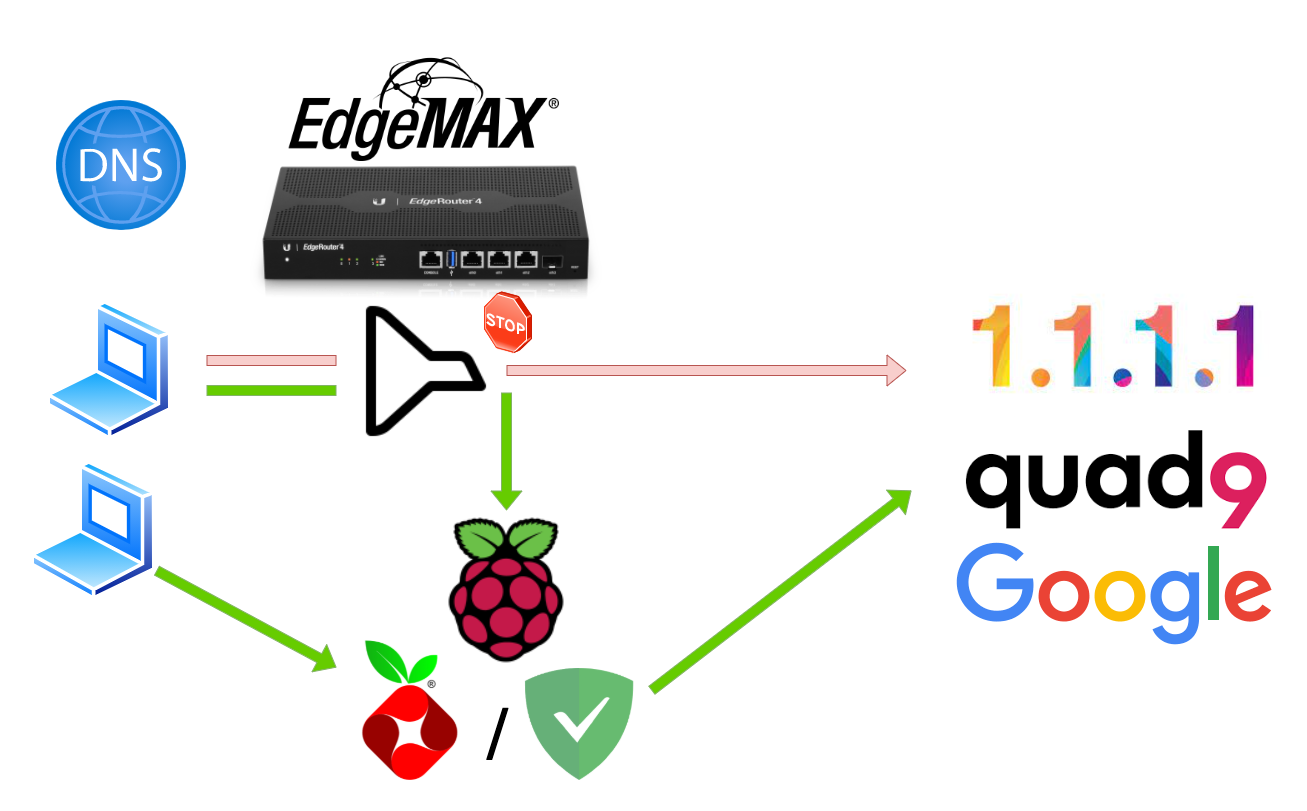
What we are trying to do
Some devices use hardcoded/forced DNS servers, so they do not follow the DHCP DNS information.
be that a google related app, or an IoT device that’s stubborn.
By using some clever firewall rules we can force all the devices that are not our DNS server ( AdGuard / Pi-Hole ) to be “redirected” towards our internal DNS server(s)
DEMO: Trying to bypass our DNS server with and without firewall rule
To show the effect of our firewall rule, we do a dig before the rule is active.
dig doubleclick.net @1.1.1.1 ;; ANSWER SECTION: doubleclick.net. 209 IN A 142.251.36.46
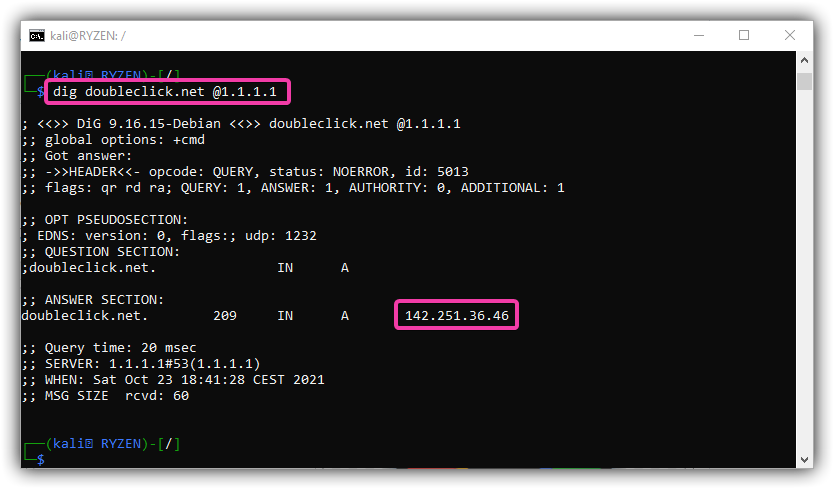
We see that by manually defining our DNS server (@1.1.1.1) we can bypass our DNS server
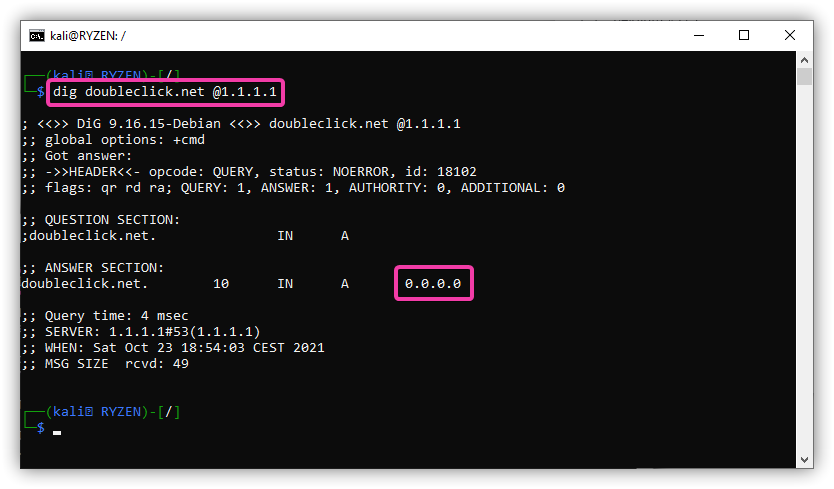
If we enable our firewall rule, this request will now be re-routed, forced over our internal DNS
dig doubleclick.net @1.1.1.1 ;; ANSWER SECTION: doubleclick.net. 10 IN A 0.0.0.0
Setting up the firewall rule(s)
- We need a DNS masquerade rule (Source NAT)
- We need a DNAT rule (Destination NAT)
Log in on the UBNT device, go to “Firewall/NAT” > “NAT” tab on top
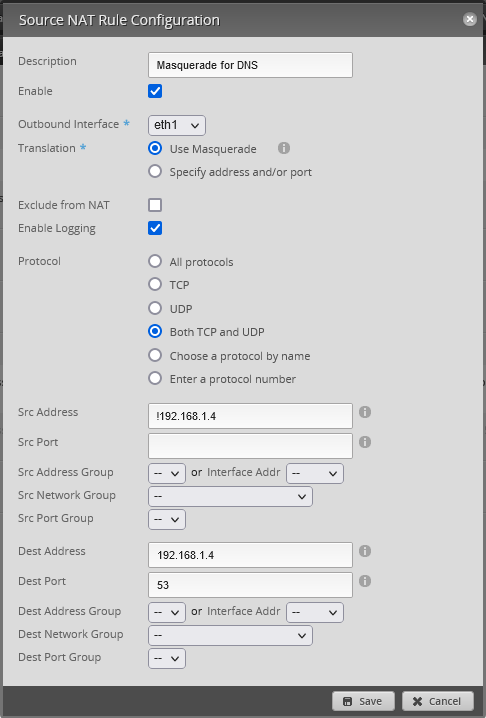
Source NAT rule
The outbound interface must be your internal interface.
eth0 is my WAN
eth1 is my LAN
The Src Address is everything but my DNS server itself.
If you have multiple DNS server you can set them with !192.168.1.4-192.168.1.5
Destination NAT rule
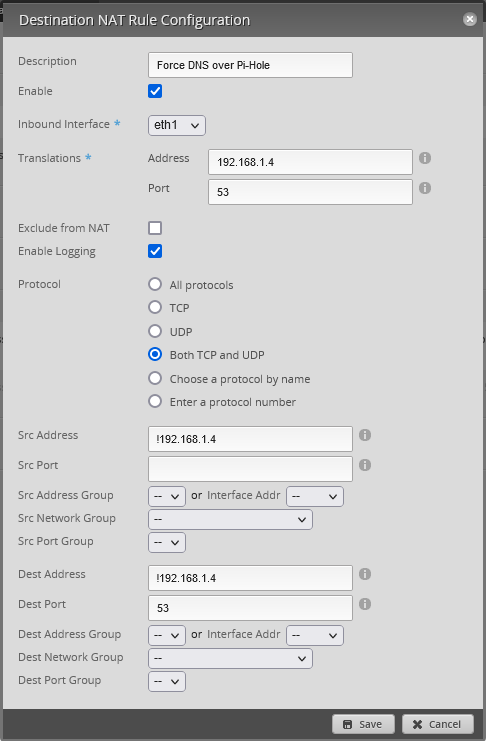
Disable logging after testing, to prevent the FW from filling up / wasting r/w cycles.
If you enable logging, you can drill down to find what device is not using your DNS, or check the rule counters
That’s it!

Hi there, looks like the “Destination NAT rule” is missing the image capture and showing a duplicate of the Source one.
Oops! Good catch!
Thanks, I’ve updated the image